Towards Automated Fuzzing of 4G/5G Protocol Implementations Over the Air (GLOBECOM 2022)
Dec 4, 2022·,,,,·
0 min read
Matheus E. Garbelini
Zewen Shang
S. Chattopadhyay
S Sumei
E Kurniawan
Abstract
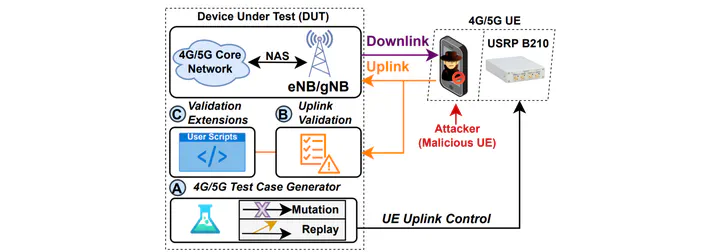
Recent rise in the mobile network communication vulnerabilities highlights the need for systematic security testing frameworks for communication protocols. In this paper, we propose a real-time framework to fully manipulate the 4G and 5G data-link and network communication to the base station (eNB/gNB). This is for experimenting and testing the security of data-link protocols such as Media Access Control (MAC), Radio Link Control (RLC), Packet Data Convergence Protocol (PDCP) and network protocols such as Radio Resource Control (RRC) and Non-access stratum (NAS). Although we focus on the base station, our framework is equally applicable for manipulating the communication to the user equipment (UE). An appealing feature of our framework is that it automatically constructs the protocol state machine during normal communication. This allows us to validate the response from the base station when it is subjected to unexpected packet sequences. Our framework also exposes an application programming interfaces (APIs) for designers to install custom attack scenarios. We have implemented our framework and used it to generate several (adversarial) scenarios that include injection of malformed and out-of-order packets as well as flooding certain packets. Our evaluation revealed crashes in OpenAirInterface (OAI) UE and gNB, as well as in Open5GS core network. Additionally, we guide our validation via the automatically constructed state machine and have caught most adversarial scenarios during our evaluation. We envision our proposed framework to provide the foundation for automated security testing of 4G/5G data-link protocol implementation.
Publication
IEEE Global Communications Conference (2022)