SweynTooth: Unleashing Mayhem over Bluetooth Low Energy (Usenix ATC)
Jul 17, 2020·,,,,·
0 min read
Matheus E. Garbelini
C. Wang
S. Chattopadhyay
S Sumei
E Kurniawan
Abstract
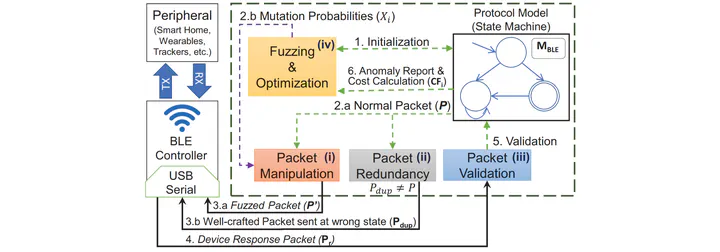
We have developed a systematic and comprehensive testing framework, which, as an automated and general-purpose approach, can effectively fuzz any BLE protocol implementation. Our framework runs in a central device and tests a BLE device when the latter gets connected to the central as a peripheral. Our framework incorporates a state machine model of the suite of BLE protocols and monitors the peripheral’s state through its responses. As of the date of publication, we have tested 12 devices from eight vendors and four IoT products, with a total of 11 new vulnerabilities discovered and 13 new Common Vulnerability Exposure (CVE) IDs assigned. We call such a bunch of vulnerabilities as SWEYNTOOTH, which highlights the efficacy of our framework.
Publication
USENIX Annual Technical Conference (2020)