AirBugCatcher: Automated Wireless Reproduction of IoT Bugs (ACSAC 2024 Prepublication)
Sep 19, 2024·,,·
0 min read
Guoqiang Hua
Matheus E. Garbelini
S. Chattopadhyay
Abstract
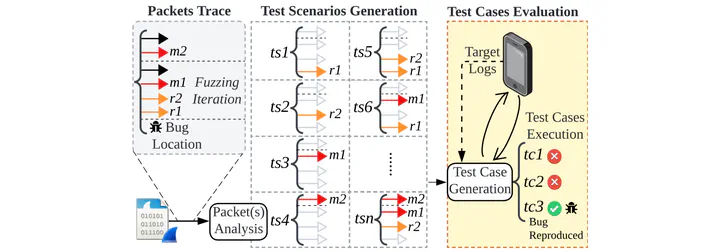
Fuzzing has been proven to be an effective tool to find implementation bugs in a range of wireless Internet of Things (IoT) devices such as smartphones, trackers, smart wearables, routers, etc. However, reliable and automated reproduction of vulnerabilities reported by over-the-air (OTA) fuzzing pipelines remains an open problem. While bug reproduction is crucial for troubleshooting and fixing of security flaws, it remains a challenge due to the non-deterministic nature of wireless devices. In this context, we present AirBugCatcher, a hardware and protocol agnostic tool to automatically identify reliable OTA attack vectors and reproduce bugs in commercial-off-the-shelf (COTS) IoT devices. AirBugCatcher aims to address two fundamental challenges during reproduction of vulnerabilities: Reproduction of bugs under the non-deterministic communication of wireless devices and resolution of ambiguities during the attack vector analysis of bugs within fuzzing logs. AirBugCatcher accomplishes this by firstly analyzing packet traces and logs from an existing fuzzing pipeline and extracting a minimal set of fuzzing packets that might be responsible for triggering bugs in the target IoT device. Subsequently, AirBugCatcher reliably reproduces bugs by generating several exploitation codes (test cases) and executing them against the target to validate the root cause of bugs. AirBugCatcher has been evaluated against four COTS IoT devices employing wireless protocols such as 5G NR, Bluetooth and Wi-Fi. The results show that AirBugCatcher can reproduce 90.4% (40/44) of bugs (crashes or hangs) extracted from fuzzing logs and generate proof of concept code that contains minimal attack vectors. For instance, AirBugCatcher only generates up to three fuzzed packets (i.e., three attack vectors) from fuzzing logs that contain ≈47K fuzzed packets. Finally, we demonstrate that a standard replay-based approach (i.e., attempting to replay all packets from fuzzing logs) fail to reproduce most bugs (15 out of 16) due to the non-deterministic nature of wireless protocol implementations. Overall, we highlight that AirBugCatcher offers a valuable addition to IoT fuzz testing pipelines by automating the process of OTA bug reproduction and empowering researchers and developers to identify and fix security flaws in IoT devices more efficiently.
Publication
Annual Computer Security Applications Conference (ACSAC 2024) (Prepublication)